Authenticator is a ELF 64 bit executable. It is dynamically linked and is not stripped for debug symbols
$ file authenticator
authenticator: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=66286657ca5a06147189b419238b2971b11c72db, not stripped
Strings shows a lot of standard stuff and a few things that are likely directly related to this challenge. There are a couple of what seem to be dialog lines, mention of a flag and a rather strange sequence of, }a:Vh|}a:g}8j=}89gV<p<}:dV8<Vg9}V<9V<:j|{:.
Since the file is not stripped, main is listed in Ghidra’s symbol tree under functions.
The program prompts for input of a username and a pin. If they are both correct, the then a success message is output. The username is show to be 11337 but the pin provided by the user is passed to another function and it’s return value is evaluated.
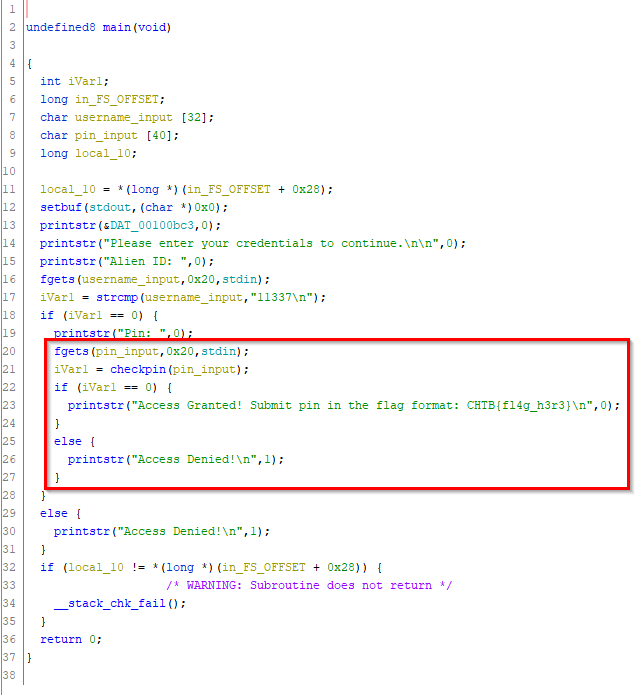
get username
if username == 11337 {
get pin
chekpin(pin)
if pin == correct value {
Suceess
}
else {
Access denied
}
}
else {
Access denied
}
In the check pin function, the odd string we noticed earlier is XOR’d with the key of 9U and the value is compared with the pin provided by the user.
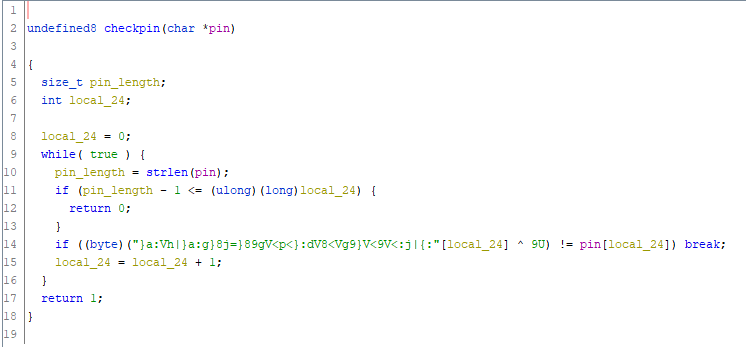
XOR }a:Vh|}a:g}8j=}89gV<p<}:dV8<Vg9}V<9V<:j|{: with 9U and the result is the value of the flag once it is wrapped in the flag format CHTB{}.
