
In Delivery, we will leverage missconfigurations in a ticketing system and internal communications channels to gain access to where we certainly shouldn’t be able to go. We will also see another example of where weak and reused passwords make our job easy.
Enumeration
Starting off with a standard NMAP scan and shows both a SSH server on port 22 and a web server on port 80.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-12 15:22 UTC
Nmap scan report for 10.10.10.222
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c:40:fa:85:9b:01:ac:ac:0e:bc:0c:19:51:8a:ee:27 (RSA)
| 256 5a:0c:c0:3b:9b:76:55:2e:6e:c4:f4:b9:5d:76:17:09 (ECDSA)
|_ 256 b7:9d:f7:48:9d:a2:f2:76:30:fd:42:d3:35:3a:80:8c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.60 seconds
Without any credentials to try for SSH, it makes the most since to tackle the web server first.
There isn’t much new here but there are links to a few other useful pages. A Helpdesk link and a contact page in that tells about a few ways to get in contact with the team.
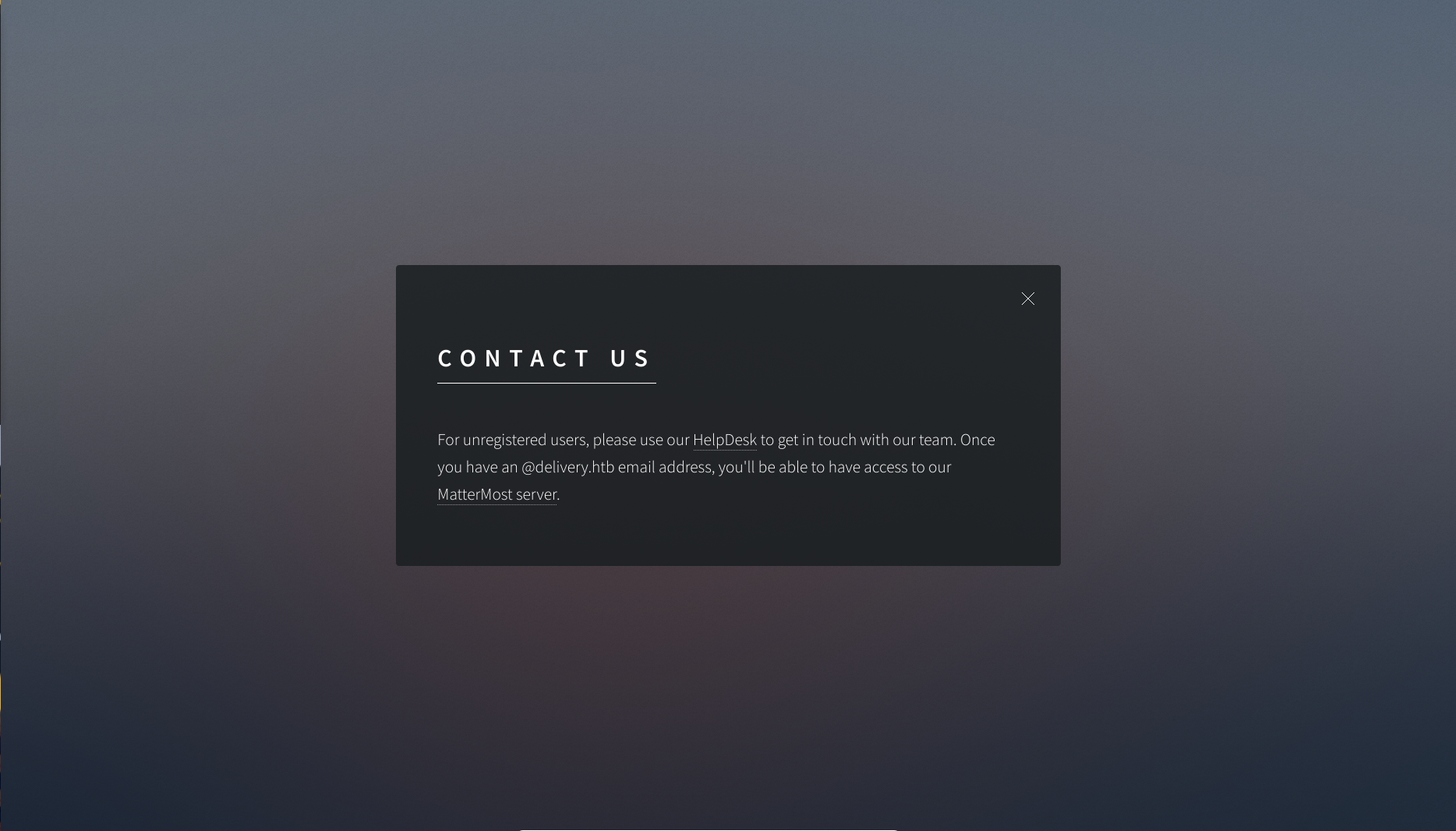
If users have a @delivery.htb email, sign up for an internal Mattermost server. Lacking that, unregistered users can open a ticket on a help desk platform.so we start by checking out the ticket system. The same one linked by from help desk on the home page.
OS Ticket
This leads to another subdomain. http://helpdesk.delivery.htb/, which means /et/hosts will need to be edited to make it reachable.
A user account is not required prior to creating a ticket. It asks for standard information, name, email address, description of the problem, and so on.
Doesn’t seem to be a whole lot here. We can pull up our ticket using the info on this page for editing and further communication and we also have an email that we could send replies too.
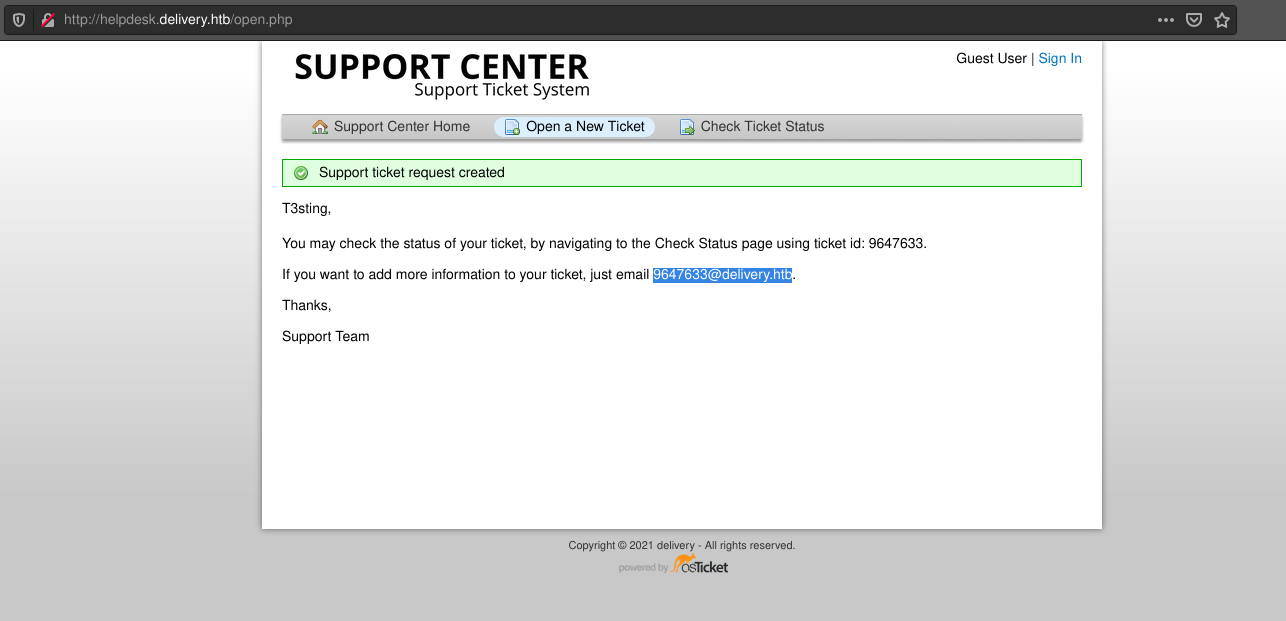
From the ticket’s status page, we can see the info we submitted to open the ticket originally.
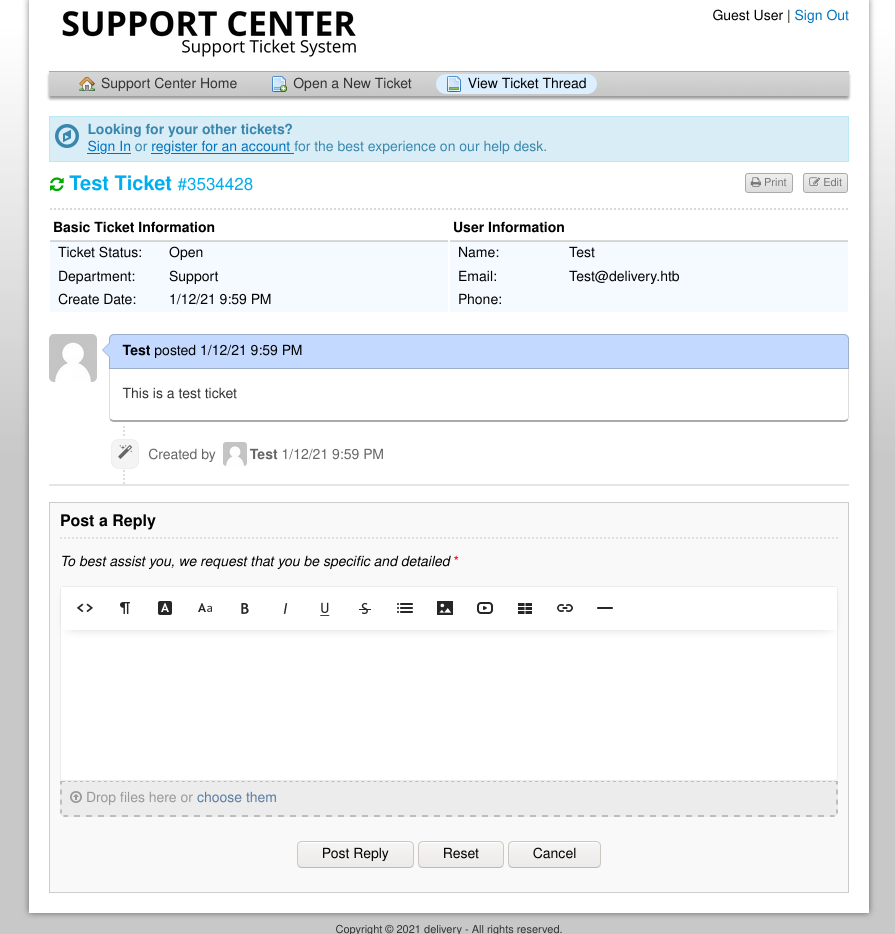
An attempt can be made to register an account, but it requires email verification. As HTB boxes are not connected to the internet, there is never going to be a confirmation email.
Foothold, Mattermost and Credential Reuse
The next thing to look at is the Mattermost instance.
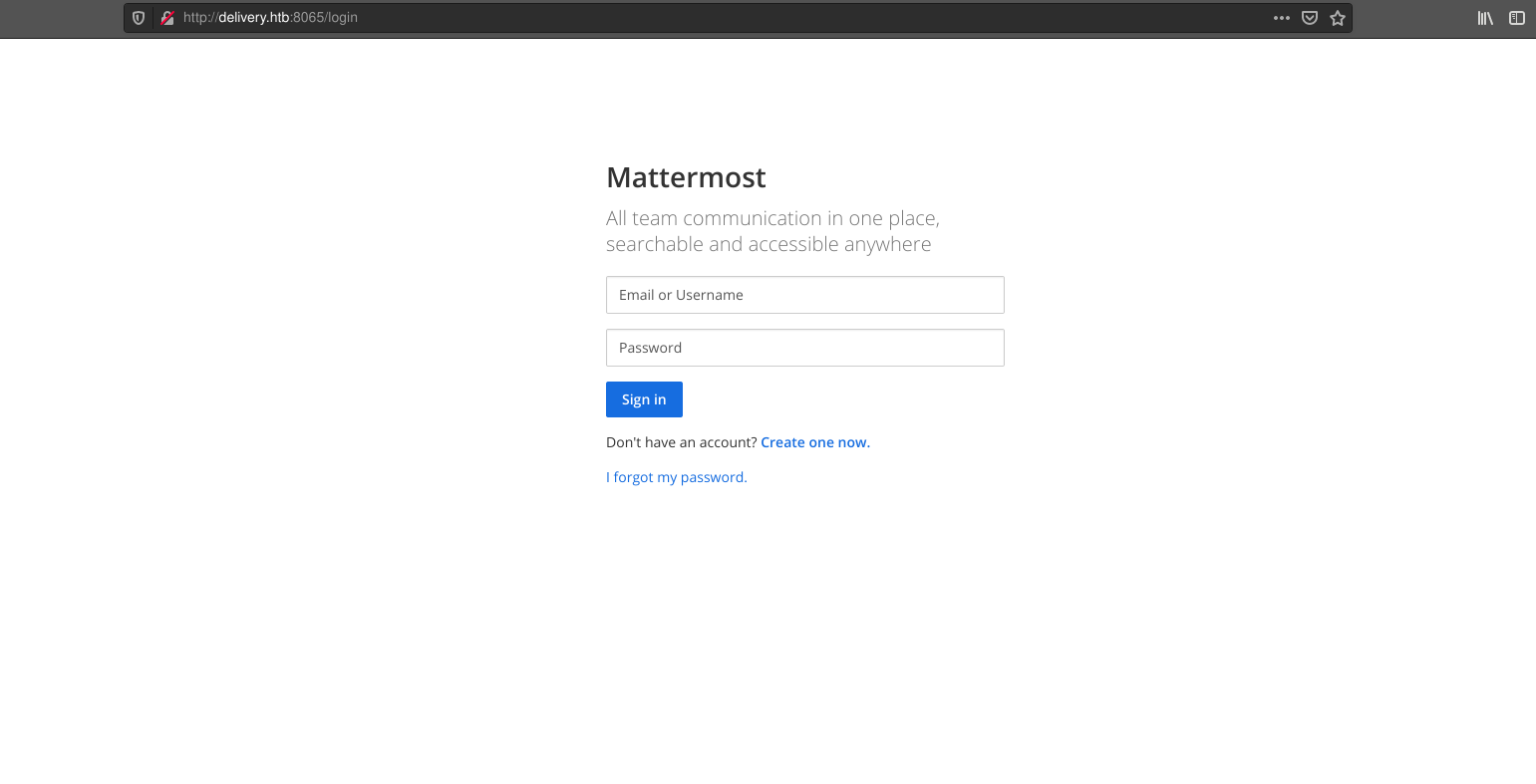
There is a login page but no credentials so far. It’s possible to attempt to register but a @delivery.htb email account is required. A fake email could be submitted.
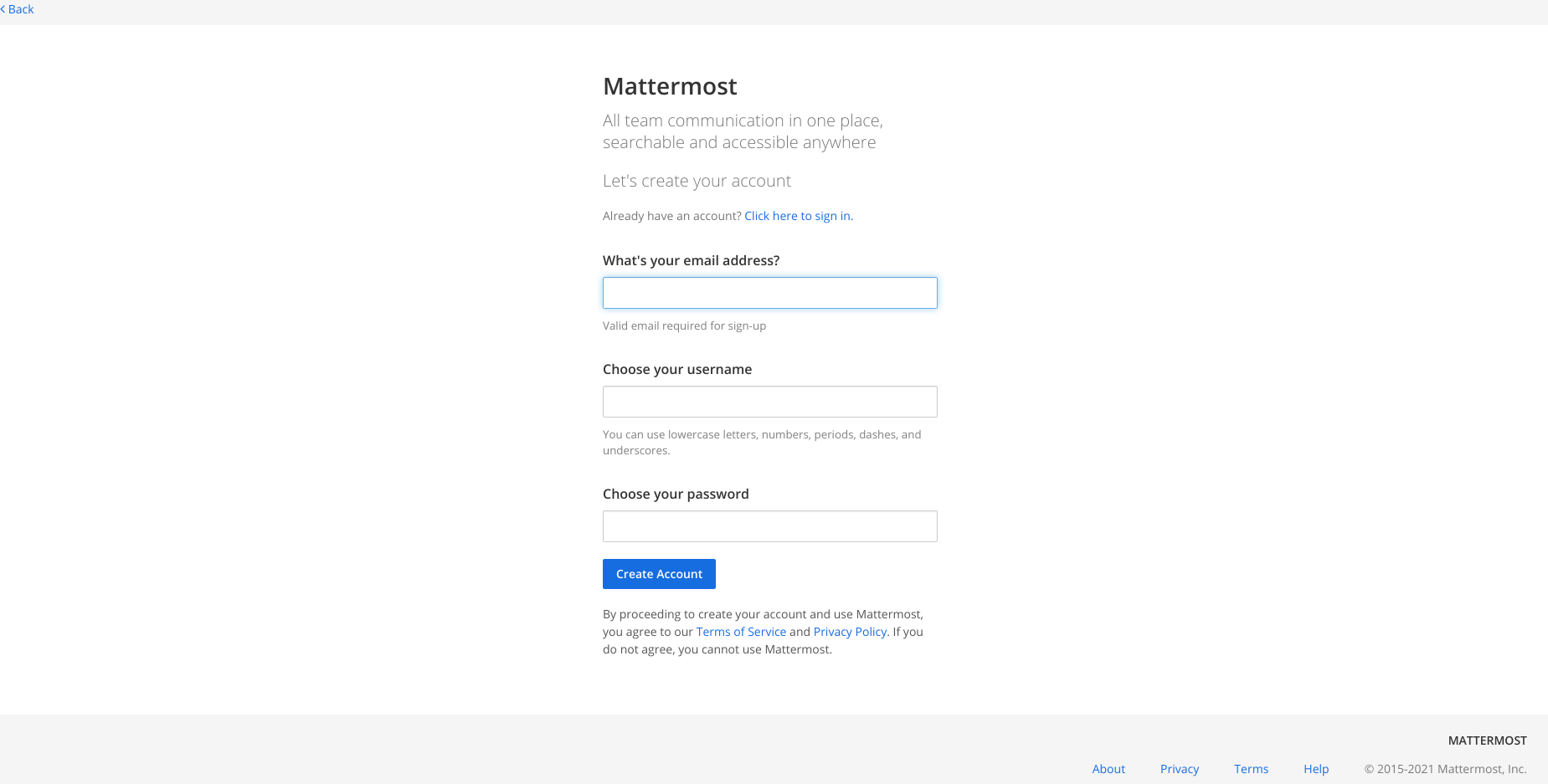
But… email verification is also required for Mattermost. It might seem to be a dead end. However, a user can register a @delivery.htb email account. It just takes a bit of creativity.
Recall the ticket created on the OS Ticket platform, it provided an email that could be send replies to the ticket. Prehapes, it can be used as a valid @deliery.htb email to register for the internal Mattermost server.
Sure enough, the email given by the support ticket can receive email confirmation’s from Mattermost.
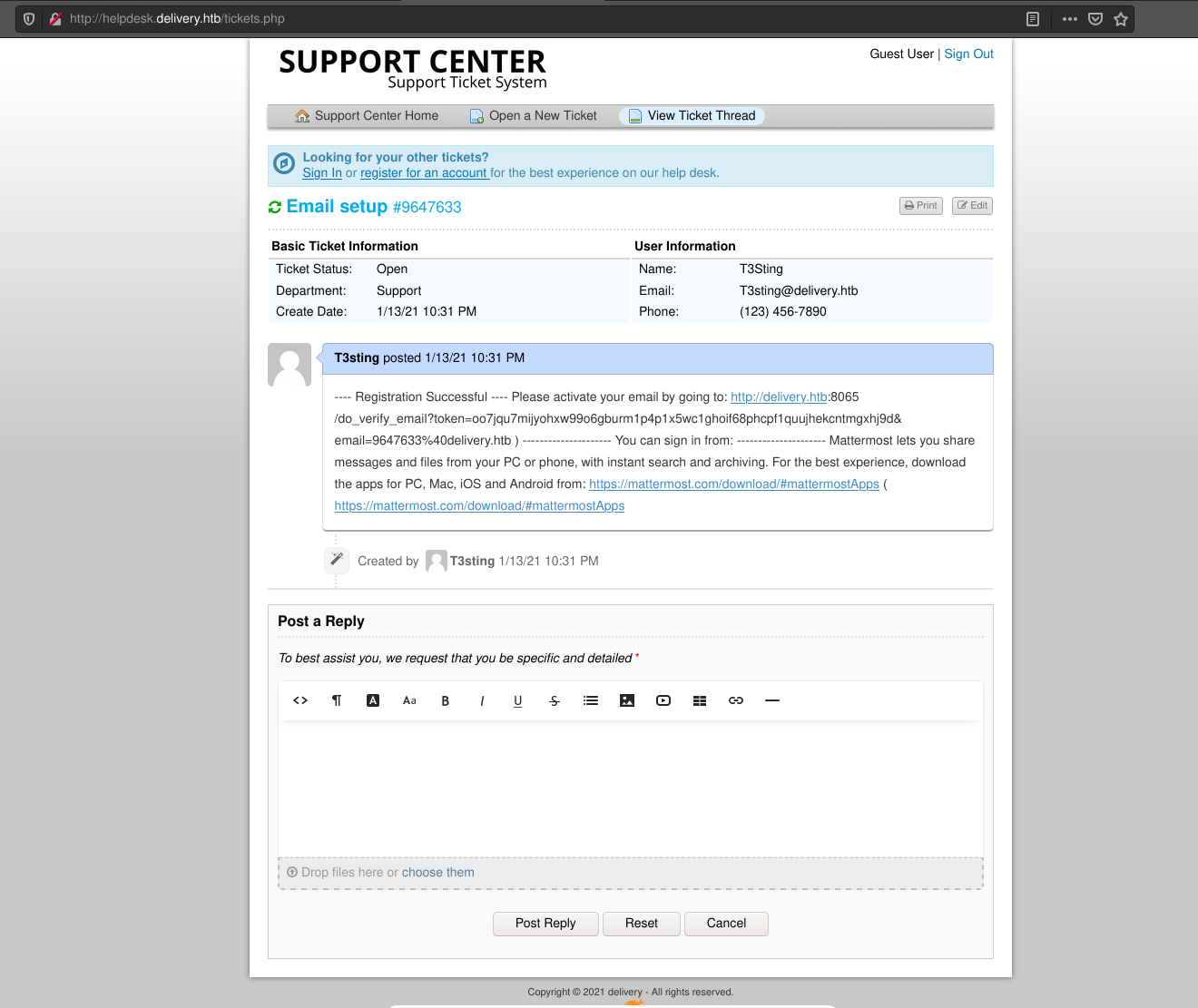
Once the an account is verified it can be used to login to Mattermost.
There are a few more steps in the account setup, including joining the Internal channel. Time to see what juicy secrets are being kept in their channels.
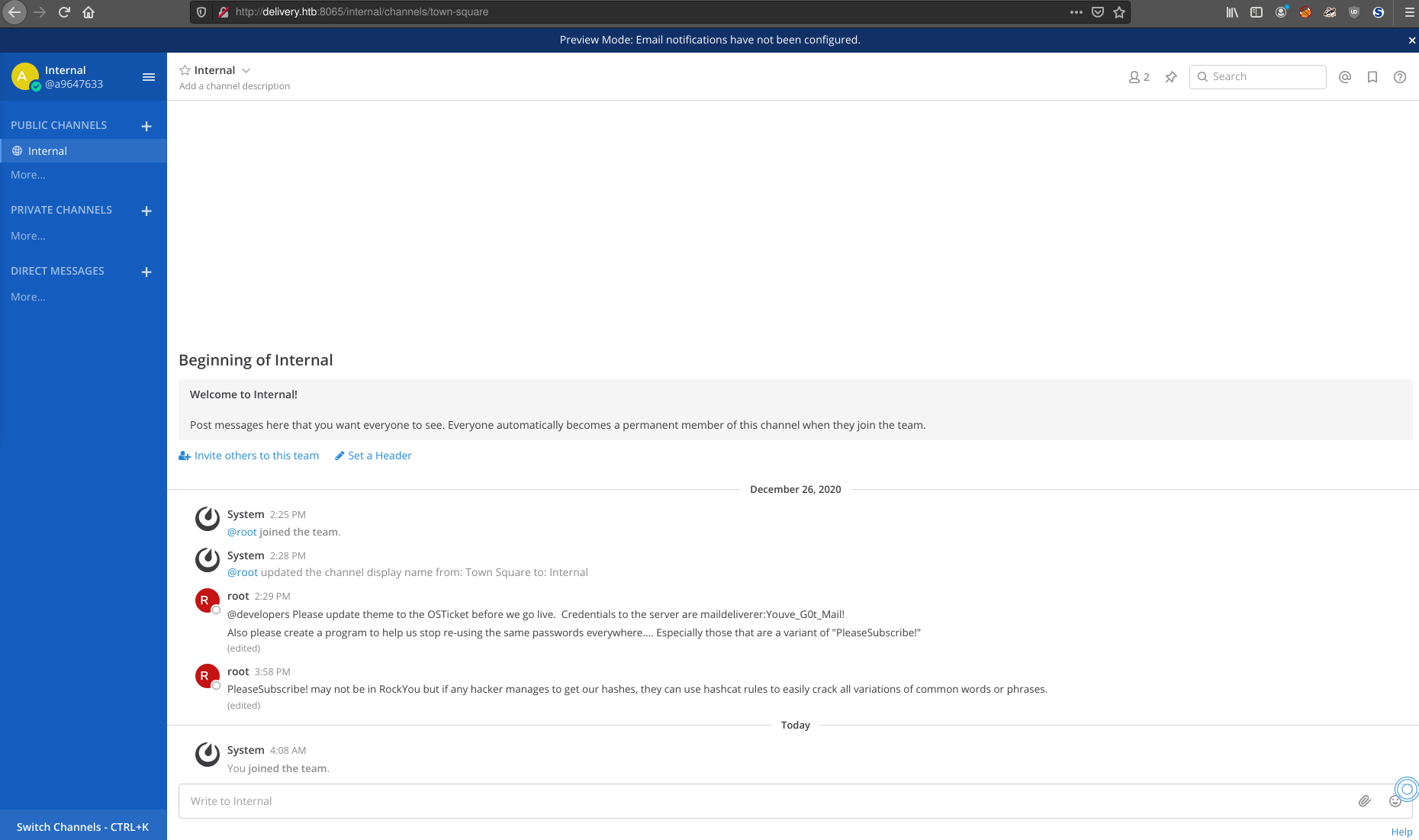
There are a few things to learn from this page. First, there are some credentials that can potentially be used to login elsewhere the OS Ticket platform and based on the conversation, they might work other places as well. maildeliverer:Youve_G0t_Mail!
The above credentials can be used to access the Agent Sign in on OS Ticket. There might be other interesting info here but there doens’t seem to be much here in this case.


However, the Mattermost channel also mentioned that password reuse was a problem. These credentials will likely work elsewhere. Turns out one such place is, SSH.
Root: Password Cracking
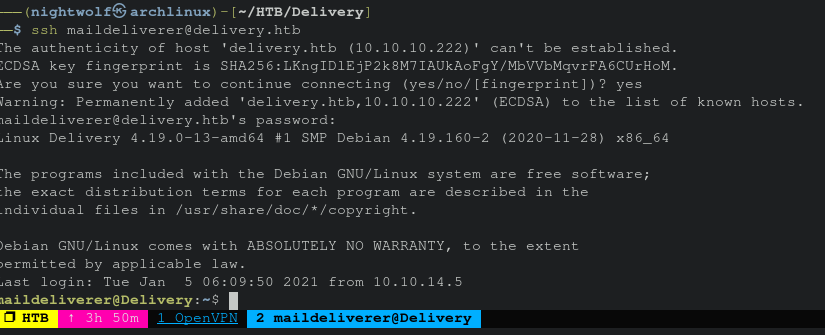
maildelivery doesn’t have any interesting groups or sudo rights. It might be able to access where Mattermost credentials are stored. That would lead to some hashes we could likely crack.
First thing to try is to check the Mattermost config.json stored in /opt/mattermost/config There the credentials Mattermost uses to interact with a local mysql database, mmuser:Crack_The_MM_Admin_PW, are found.
These can be used to login into the local mysql instance.
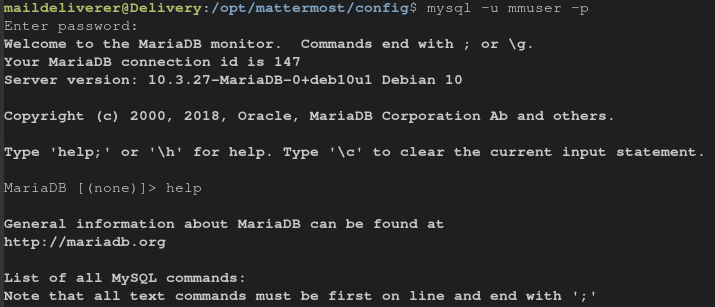
Listing the databases shows there is one for Mattermost. Among the tables it contains, is one for users.
Select the username and password fields and listing the contents to reveal the hash for the “root” user.
MariaDB [mattermost]> select Username, password from Users;
+----------------------------------+--------------------------------------------------------------+
| Username | password |
+----------------------------------+--------------------------------------------------------------+
| surveybot | |
| c3ecacacc7b94f909d04dbfd308a9b93 | $2a$10$u5815SIBe2Fq1FZlv9S8I.VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |
| 5b785171bfb34762a933e127630c4860 | $2a$10$3m0quqyvCE8Z/R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |
| root | $2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO |
| ff0a21fc6fc2488195e16ea854c963ee | $2a$10$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS.Pduq |
| channelexport | |
| 9ecfb4be145d47fda0724f697f35ffaf | $2a$10$s.cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |
| a9647633 | $2a$10$NPohGjjgCpRgA6fyFTnKhO5Y4l5XZchc7ax5mcOplVPU/qN/KjQri |
+----------------------------------+--------------------------------------------------------------+
On the internal Mattermost channel, it was mentioned that “PleasSubcribe!” was probably used a lot and though it wasn’t in rockyou.txt the admin thought it could be cracked pretty trivially with some rules.
Before it can be cracked, the hash type needs to be identified. Hash identifier can typically get you on the right track with these and this one is predicted to be bcrypt.
Rules are a way to create variations of Passwords without needing a larger password file. They can be things like adding 1234 at the end of a password or exchanging “a” for “@”. Hashcat includes a number of rules configuration files and they can be a good starting point. Next a “wordlist” with the single the single password, “PleaseSubscribe!” is created.
.\hashcat64.exe -a 0 -m 3200 .\hashes_in.txt .\wordlist.txt -r .\rules\base64.rule
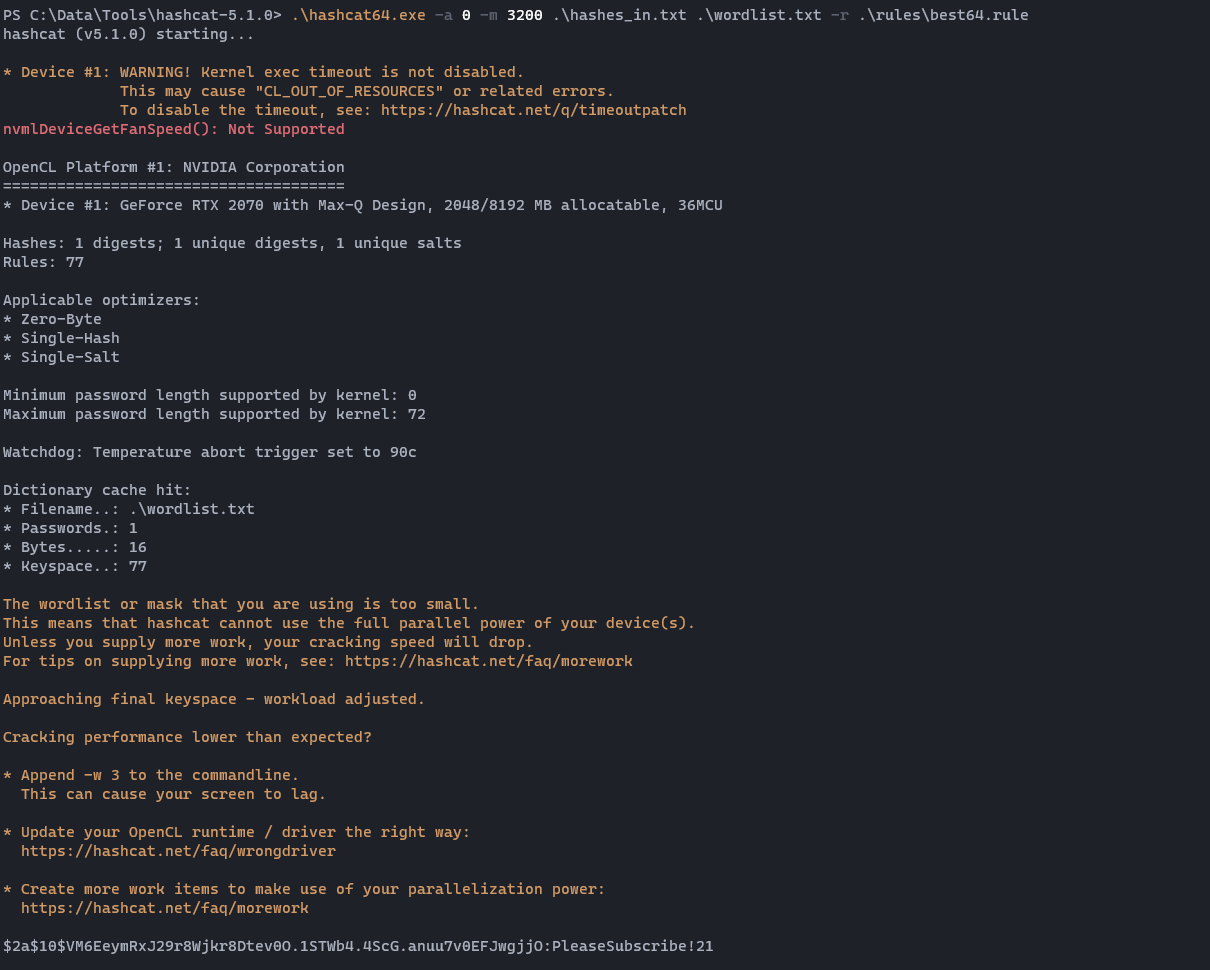
A result comes back pretty quickly.root:PleaseSubscribe!21 That can be used to login over SSH and gain full access over the machine.
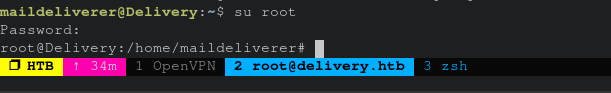
note.txt
IppSec left a note.txt providing some more context and inspiration behind the foothold on this box. I highly recommend giving it a read.
root@Delivery:~# cat note.txt
I hope you enjoyed this box, the attack may seem silly but it demonstrates a pretty high risk vulnerability I've seen several times. The inspiration for the box is here:
- https://medium.com/intigriti/how-i-hacked-hundreds-of-companies-through-their-helpdesk-b7680ddc2d4c
Keep on hacking! And please don't forget to subscribe to all the security streamers out there.
- ippsec
In the spirit of the note, here are some cybersecurity streamers and YouTubers I would recommend checking out.
IppSec , the creator or this box, releases a video writeups for HTB boxes are they retire. They are very well put together and I would highly recommend checking them out for HTB or using his site to lookup specific tools or situations you might encounter.
John Hammond posts video writeups for various CTFs and wargames. Awesome friendly guy and I totally recommend checking him out especially if you are looking to get started as a beginner.
LiveOverflow makes videos on various CTF challenges and also dug into several other topics in some short series including, hardware security research, browser exploitation, Pwn Adventure 3 (a game designed for hacking) and a whole lot more.
StackSmashing has done some really cool things in relation to hardware, reverse engineering, and hacking handheld game devices. There is also a few on reversing WannaCry and one about reversing and modifying an IoT Camera.
Gynvael streams regularly each week on various cyber security topics. One things about it is because it is a live stream, you get a chance to see raw work flow and methodology.
Gamozo Labs does a lot of low level programming. His tool of choice is Rust and he has a lot of cool projects to show from writing an OS to a kernel exploit for an older version of Android. I won’t claim to understand everything he is doing but it’s very fun to hang around and I still manage to pick up bits and pieces. He posts many of his past streams on YouTube .
PwnFunction has some really awesome dives explaining various web vulnerabilities, what causes them and how to exploit them. Recently he has also been working on a Binary Exploitation series.
If you are looking for even more cybersecurity content creators, check out this video -> https://www.youtube.com/watch?v=GSraDuD4ziQ
Wrap up
This box is probably one of my favorites simply because the foothold was so satisfying once I figured out and yet incredibly simple. I really appreciate IppSec taking the time to make this box and include the note about the inspiration. Hopefully, it was insightful for the rest of you as well.
